使用Teleport管理服务器
简介最近想把公司的内网几台服务器能通过打开一个网站的方式进行管理,所以寻求了一圈最终选择了Teleport。Teleport,这是一个使用Go语言编写的,高效的现代SSH管理工具。
Teleport 是一款可以替代 SSH 工具的新一代服务器集群管理工具,它不仅可以同时管理大量服务器还可以作为一个终端录制工具,它提供了一个直观的 Web 界面来显示终端,也就是说你可以在浏览器操作服务器,在浏览器录制、分享。它是开源的,它运行在你的服务器上。
本文主要介绍如何安装和使用Teleport。
一、安装Teleport
1.1、下载
下载页面:https://gravitational.com/teleport/download/
wget https://get.gravitational.com/teleport-v4.2.4-linux-amd64-bin.tar.gz
1.2、申请一个https证书
teleport必须要通过https进行访问,所以要申请一个https证书
该过程读者自行处理,我这里通过certbot来申请的免费证书
1.3、解压并进入到解压后的目录
tar -zxvf teleport-v4.2.4-linux-amd64-bin.tar.gz -C /home/ cd /home/teleport
1.4、生成配置文件
./teleport configure > teleport.yaml
配置文件内容
[root@localhost teleport]# cat teleport.yaml
#
# Sample Teleport configuration file.
#
teleport:
nodename: local-178 #修改节点名称,以便后续自己好分辨
data_dir: /var/lib/teleport
pid_file: /var/run/teleport.pid
auth_token: cluster-join-token
auth_servers:
- 0.0.0.0:3025
connection_limits:
max_connections: 15000
max_users: 250
log:
output: stderr
severity: INFO
ca_pin: ""
auth_service:
enabled: "yes"
listen_addr: 0.0.0.0:3025
tokens:
- proxy,node:cluster-join-token
session_recording: ""
client_idle_timeout: 0s
disconnect_expired_cert: false
keep_alive_count_max: 0
ssh_service:
enabled: "yes"
labels:
db_role: master
db_type: postgres
commands:
- name: hostname
command: [/usr/bin/hostname]
period: 1m0s
- name: arch
command: [/usr/bin/uname, -p]
period: 1h0m0s
proxy_service:
enabled: "yes"
listen_addr: 0.0.0.0:3023
web_listen_addr: 0.0.0.0:3080
tunnel_listen_addr: 0.0.0.0:3024
https_key_file: /etc/letsencrypt/live/tower.local.xxxxx.cn/privkey.pem #证书配置修改
https_cert_file: /etc/letsencrypt/live/tower.local.xxxxxx.cn/fullchain.pem #证书配置修改
1.5、运行
nohub ./teleport start -c teleport.yaml &
目前为止我们基本就安装完成了,可以通过浏览器进行访问 http://tower.local.xxxxx.cn:3080/
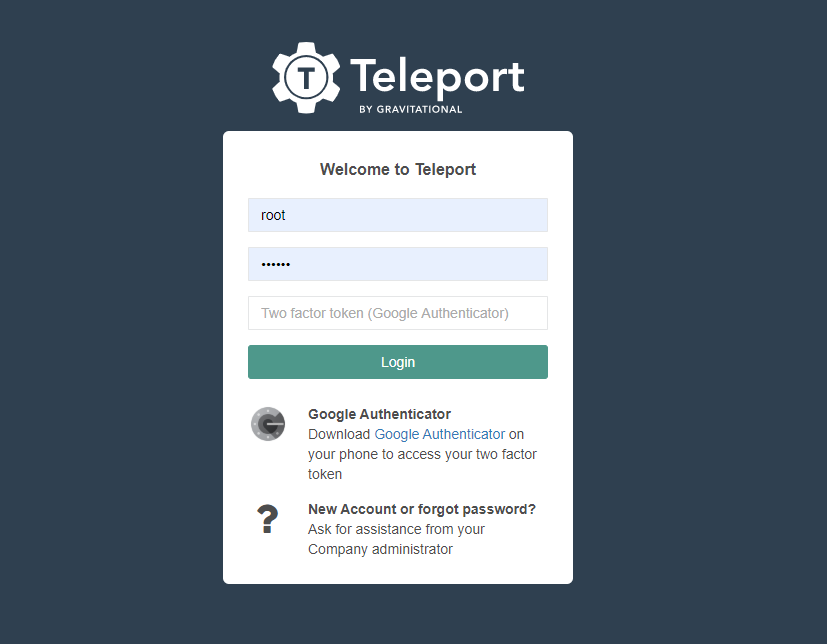
出现如上界面即可。
二、Teleport使用
2.1、首先需要创建一个用户
[root@localhost teleport]# ./tctl users add $USER Signup token has been created and is valid for 1 hours. Share this URL with the user: https://localhost.localdomain:3080/web/newuser/4c1ea9d2b14642ca5660c1e3dcd21185 NOTE: Make sure localhost.localdomain:3080 points at a Teleport proxy which users can access.
这里我们以$USER创建一个用户。
2.2、打开上一个步骤的地址(域名需要更换)
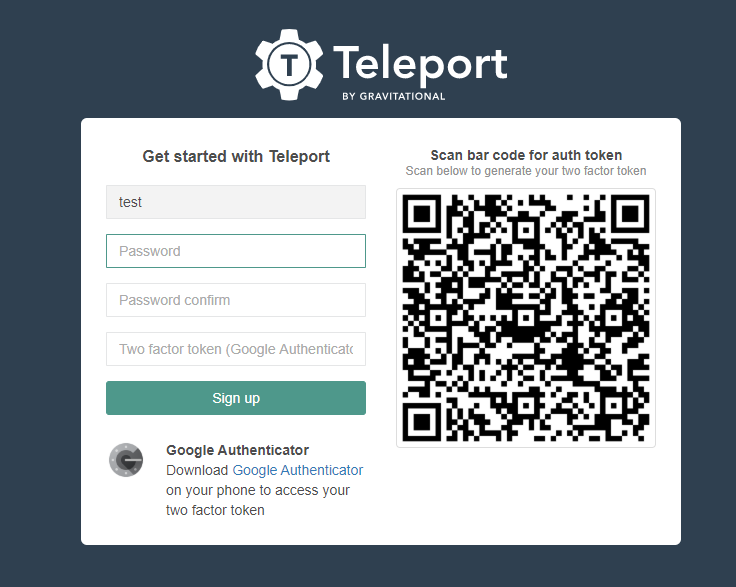
这里很关键,这里需要去下载谷歌的【身份验证器】,然后通过验证器去扫描二维码即可,然后根据验证器上的token填写过来即可(隔一会就会更换,安全性大大增强)。登录的时候也需要哟!
登录进入后,我们只看到一台服务器在里面,那么我们想管理更多的服务器该如何办呢?那么我们需要增加节点
2.3、增加节点
[root@localhost teleport]# ./tctl nodes add
The invite token: 11a24e45523bd2fca058cd5bd388a6fa
This token will expire in 30 minutes
Run this on the new node to join the cluster:
> teleport start \
--roles=node \
--token=11a24e45523bd2fca058cd5bd388a6fa \
--ca-pin=sha256:c46200376351d532828044858dc547690523ebf58b2e24ac6ef3d89a4c2f6414 \
--auth-server=192.168.1.178:3025
Please note:
- This invitation token will expire in 30 minutes
- 192.168.1.178:3025 must be reachable from the new node
里面已经告诉了我们如何去启动节点的命令,然后通过命名去启动即可。注意,如果我们在启动节点的过程中出现如下提示:
ERRO [PROC:1] Node failed to establish connection to cluster: Get https://192.168.1.178:3025/v1/webapi/find: x509: cannot validate certificate for 192.168.1.178 because it doesn't contain any IP SANs. time/sleep.go:149
请移除节点下/var/lib/teleport目录重新执行。
2.4、tctl帮助文档
[root@localhost teleport]# ./tctl -h Usage: tctl [<flags>] <command> [<args> ...] CLI Admin tool for the Teleport Auth service. Runs on a host where Teleport Auth is running. Flags: -d, --debug Enable verbose logging to stderr -c, --config Path to a configuration file [/etc/teleport.yaml] --auth-server Address of the auth server [127.0.0.1:3025]. Can be supplied multiple times -i, --identity Path to the identity file exported with 'tctl auth sign' Commands: help Show help. users add Generate a user invitation token users ls List all user accounts users rm Deletes user accounts nodes add Generate a node invitation token nodes ls List all active SSH nodes within the cluster tokens add Create a invitation token tokens rm Delete/revoke an invitation token tokens ls List node and user invitation tokens auth export Export public cluster (CA) keys to stdout auth sign Create an identity file(s) for a given user auth rotate Rotate certificate authorities in the cluster create Create or update a Teleport resource from a YAML file rm Delete a resource get Print a YAML declaration of various Teleport resources status Report cluster status top Report diagnostic information requests ls Show active access requests requests approve Approve pending access request requests deny Deny pending access request requests create Create pending access request requests rm Delete an access request version Print cluster version
 打包出现如下错误:Error: Application entry file "dist\electron\main.js" in the "D:\gui\demo2\build\win-unpacked\resources\app.asar" does not exist. Seems like a wrong configuration.
打包出现如下错误:Error: Application entry file "dist\electron\main.js" in the "D:\gui\demo2\build\win-unpacked\resources\app.asar" does not exist. Seems like a wrong configuration. 前一篇博客中已经说过Golang对Gzip的处理,其实这是我的服务器端的处理,那么当我们服务器返回Gzip压缩的字符串后,客户端如何进行解压呢?本文主要记录下JavaScript对Gzip进行压缩和解压处理。
前一篇博客中已经说过Golang对Gzip的处理,其实这是我的服务器端的处理,那么当我们服务器返回Gzip压缩的字符串后,客户端如何进行解压呢?本文主要记录下JavaScript对Gzip进行压缩和解压处理。 nodejs中使用npm和yarn,使用最新阿里云镜像 aliyun mirror,网上很多还是文章用的是下面这个地址~~yarn config set registry https://registry.npm.taobao.org~~
nodejs中使用npm和yarn,使用最新阿里云镜像 aliyun mirror,网上很多还是文章用的是下面这个地址~~yarn config set registry https://registry.npm.taobao.org~~ 最近想把公司的内网几台服务器能通过打开一个网站的方式进行管理,所以寻求了一圈最终选择了Teleport。Teleport,这是一个使用Go语言编写的,高效的现代SSH管理工具。
最近想把公司的内网几台服务器能通过打开一个网站的方式进行管理,所以寻求了一圈最终选择了Teleport。Teleport,这是一个使用Go语言编写的,高效的现代SSH管理工具。 Python调用WPS把文档转换PDF,并把PDF转图片,首先需要安装WPS,然后利用pypiwin32把文档转化成PDF,再利用fitz、PyMuPD把PDF转化成图片
Python调用WPS把文档转换PDF,并把PDF转图片,首先需要安装WPS,然后利用pypiwin32把文档转化成PDF,再利用fitz、PyMuPD把PDF转化成图片 快速生成表格
快速生成表格 在使用Git的过程中,不想每次都输入用户名和密码去拉取代码,所以就需要保存这些信息,那么既然有保存了,就必须有清除功能。
在使用Git的过程中,不想每次都输入用户名和密码去拉取代码,所以就需要保存这些信息,那么既然有保存了,就必须有清除功能。 在Mac电脑中,如何对Git的用户名和密码进行修改呢?起初不懂Mac,所以整了很久,本文将记录如何对这个进行操作,以便后期使用。
在Mac电脑中,如何对Git的用户名和密码进行修改呢?起初不懂Mac,所以整了很久,本文将记录如何对这个进行操作,以便后期使用。 Docker编译镜像出现:fetch http://dl-cdn.alpinelinux.org/alpine/v3.12/main/x86_64/APKINDEX.tar.gz
ERROR: http://dl-cdn.alpinelinux.org/alpine/v3.12/main: temporary error (try again later)
WARNING: Ignoring APKINDEX.2c4ac24e.tar.gz: No such file or directory问题
Docker编译镜像出现:fetch http://dl-cdn.alpinelinux.org/alpine/v3.12/main/x86_64/APKINDEX.tar.gz
ERROR: http://dl-cdn.alpinelinux.org/alpine/v3.12/main: temporary error (try again later)
WARNING: Ignoring APKINDEX.2c4ac24e.tar.gz: No such file or directory问题